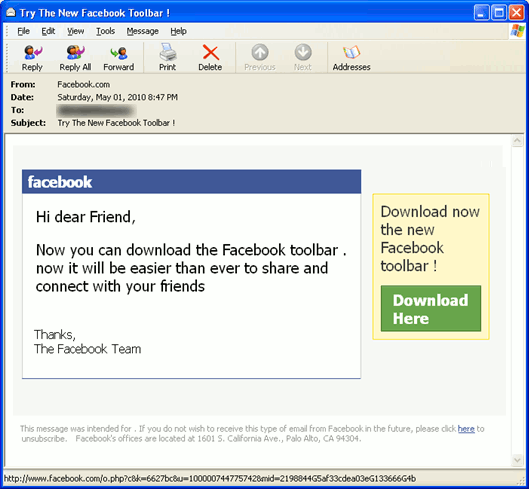
Un nuevo tipo de programa maligno infecta computadoras que comparten archivos en la red y publica el historial de páginas visitadas en un sitio internet para luego chantajear al usuario que quiera retirar su nombre de éste.
El virus troyano japonés se instala en las computadoras que utilizan el popular servicio de intercambio de archivos conocido como Winni y que es utilizado por hasta 200 millones de personas.
El virus se fija en aquellas descargas ilegales de copias de juegos del género hentai, una caricatura japonesa pornográfica.
El sitio internet Yomiuri afirma que, hasta ahora, 5.500 usuarios reconocen haber sido infectados.
Conocido como Kenzero, el virus está siendo monitoreado por la firma de seguridad cibernértica Trend Micro en Japón.
Haciéndose pasar como una instalación de pantalla de juegos, le pide al usuario de la computadora sus datos personales.
Luego procede a tomar imágenes de páginas visitadas y las publica en línea con el nombre del usuario, antes de enviar un correo electrónico exigiendo un pago con tarjeta de crédito de US$10 para "resolver su violación de las leyes de derechos de autor" y retirar la página.
Banda criminal
El sitio en el que se publica el historial le pertenece a una empresa ficticia llamada Romancing Inc. Está registrada bajo el pseudónimo de Shoen Overns.
"Anteriormente hemos visto ese nombre asociado a los virus troyanos Zeuz y Koobface. Se trata de una banda criminal establecida que sigue involucrada en este tipo de actividad", dijo Rik Ferguson, alto asesor de seguridad de Trend Micro.
Añadió que Kensero es una forma de ransomeware (virus extorsionista) que infecta la computadora y codifica los documentos, imágenes y música almacenadas, antes de exigir un pago para suministrar una clave decodificadora.
Ferguson señala que hay una variante que está afectando a usuarios en Europa.
Una organización ficticia que se denomina la fundación de derechos de autor ICPP emite pop-ups (ventanas emergentes) y correos después de que el virus inspecciona el disco duro de la computadora para contenido ilegal - aún no encuentre nada.
Luego ofrece llegar a un "arreglo preliminar al juicio" de US$400, pagables por tarjeta de crédito y advierte de costosos casos en los tribunales e, inclusive, carcel para aquellas víctimas que ignoren la oferta.
Sin embargo, en lugar de tomar el dinero, la organización vende los detalles de la tarjeta de crédito, explica Fergusson.
Este aconseja ignorar el chantaje y utilizar un programa gratis en línea para escanear y detectar los programas malignos. Añade que siempre es mejor descargar contenido de sitios confiables.
Fuente BBC
 Y aunque aparentemente parezcan un simple juguete lo cierto es que hay una aplicacion que se les desea dar que aunque parece simple y sencilla es una excelente idea en caso de algu tipo de desastre, y es que por mas que este la telefonia celular en su auge lo cierto es que cuando hay un huracan un terremoto o algun fenomeno natural causando un cataclismo las comunicaciones y enlaces de radio tienden a perderse a consecuencia directa del daño de las torres de celular o bien de las mismas torres de comunicacion; por lo que obtener datos en una locacion remota puede hacerse muy muy dificil aun dias despues de haberse sucitado el cataclismo. Es por eso que se plantea la posibilidad de enviar drones en ejmabres a fin de que se puedan establecer una red o varias redes dinamicas de comunicacion; y esto es lo que se esta logrando con el proyecto SMAVNET del Instituto federal de Tecnologia en Suiza, esto basado en las capacidades que tienen los drones que anteriormente hablamos son bastante practicos para lograr su fin
Y aunque aparentemente parezcan un simple juguete lo cierto es que hay una aplicacion que se les desea dar que aunque parece simple y sencilla es una excelente idea en caso de algu tipo de desastre, y es que por mas que este la telefonia celular en su auge lo cierto es que cuando hay un huracan un terremoto o algun fenomeno natural causando un cataclismo las comunicaciones y enlaces de radio tienden a perderse a consecuencia directa del daño de las torres de celular o bien de las mismas torres de comunicacion; por lo que obtener datos en una locacion remota puede hacerse muy muy dificil aun dias despues de haberse sucitado el cataclismo. Es por eso que se plantea la posibilidad de enviar drones en ejmabres a fin de que se puedan establecer una red o varias redes dinamicas de comunicacion; y esto es lo que se esta logrando con el proyecto SMAVNET del Instituto federal de Tecnologia en Suiza, esto basado en las capacidades que tienen los drones que anteriormente hablamos son bastante practicos para lograr su fin